Drowning in Data.
Starving for Context.
Security teams are drowning in alerts, detection findings, threat reports, and raw telemetry. Most of the work to investigate them is spent on data collection, context gathering, correlation and it’s painfully manual.
Analysts burn out on repetitive triage. Senior talent wastes time pivoting between tools chasing valuable context. Answers live in silos across EDR tools, SIEMs, network & cloud logs, vulnerability scanners and more.
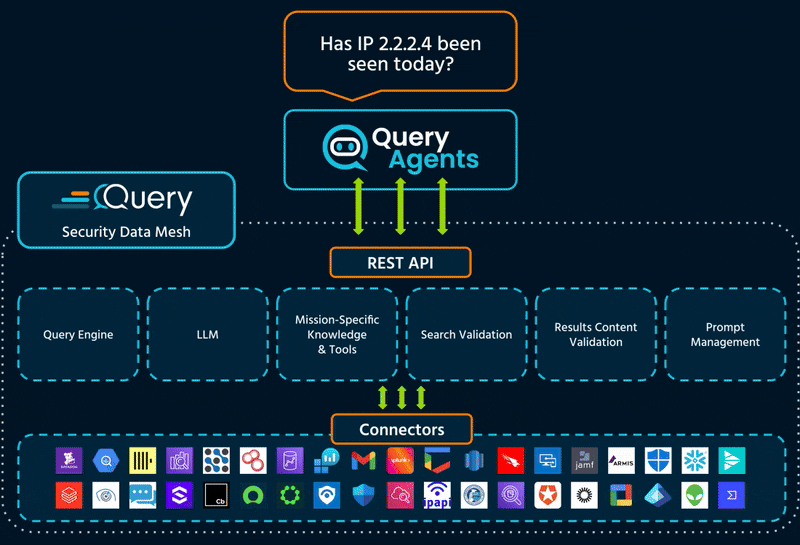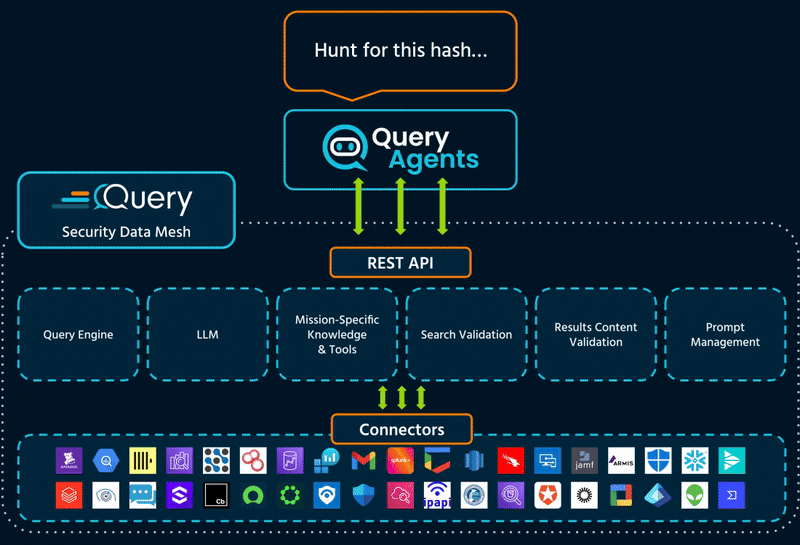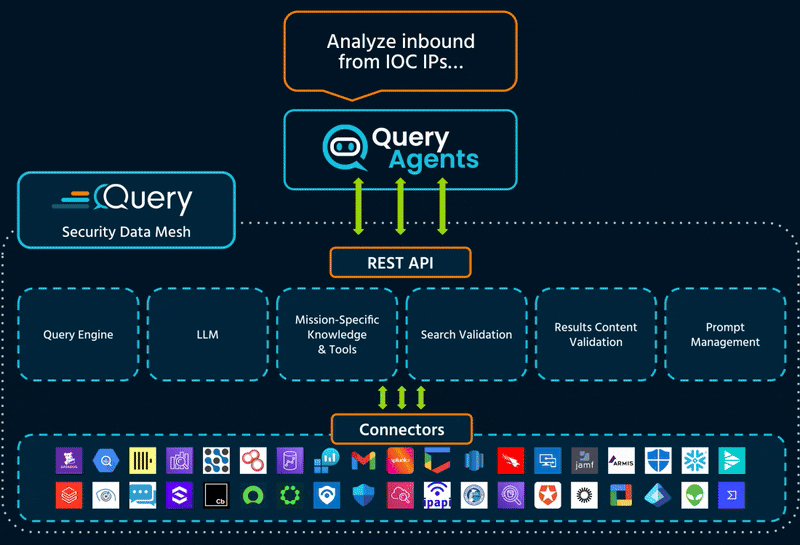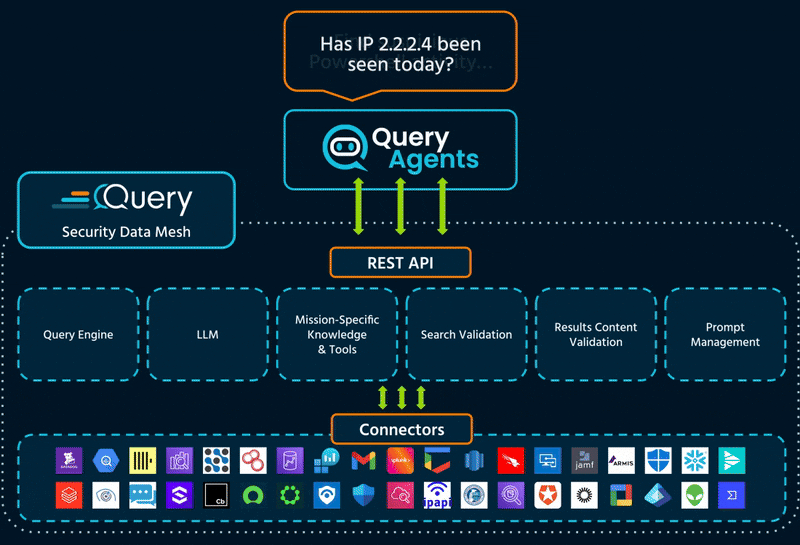
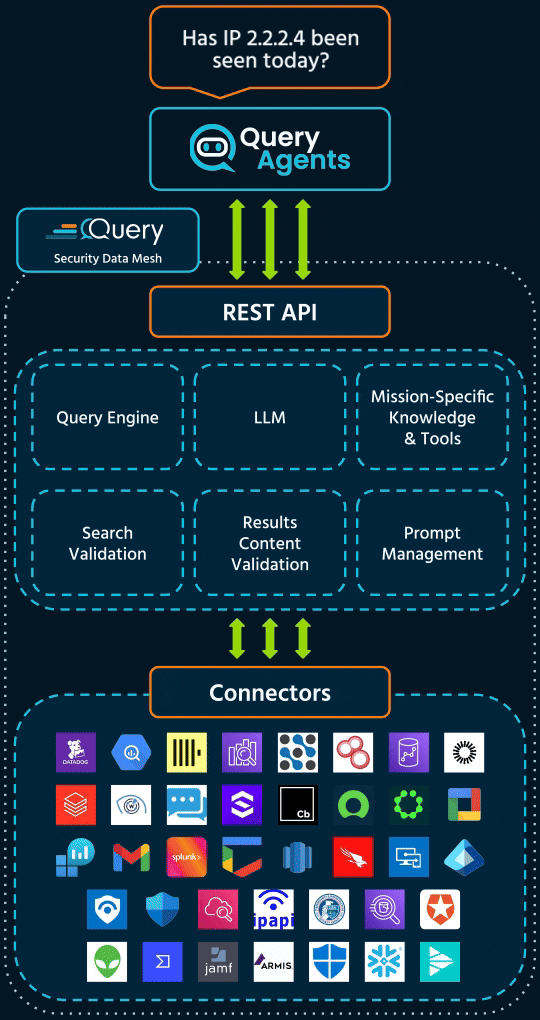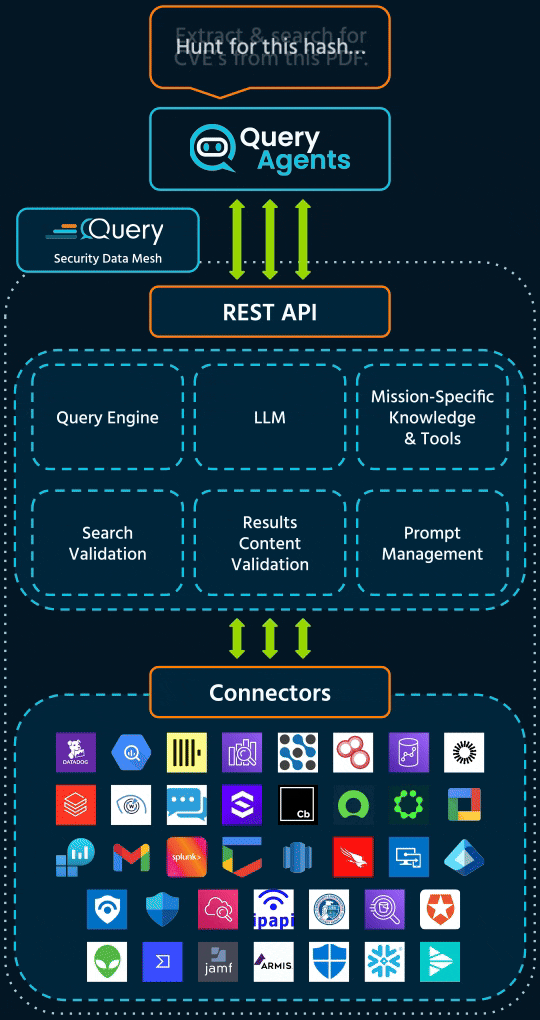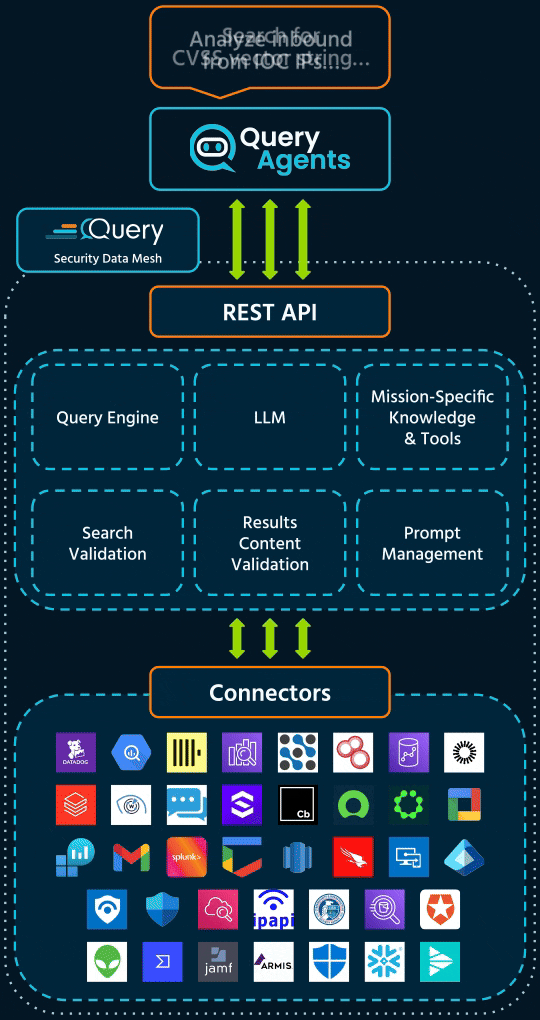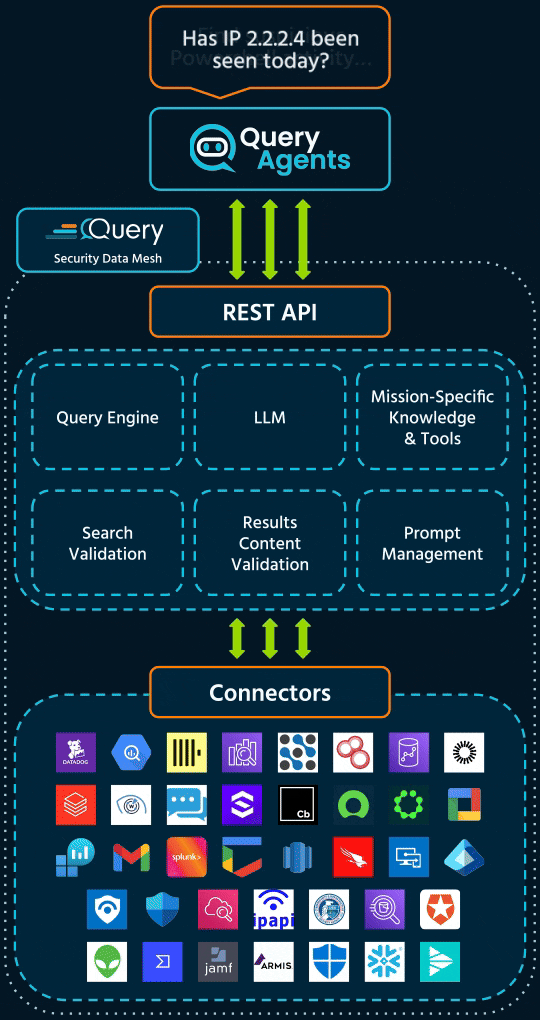
Query changes this mode of operation by combining mission-specific Agents with real-time access to data from our Security Data Mesh.
Each Agent Is Built to Do One Job, Exceptionally Well
Each Query Agent is purpose-built to do a specific job in security operations: triage, threat hunting, enrichment, and investigation.
What sets them apart isn’t just the logic, it’s the data. Every Agent is powered by real-time access to AI-ready data from the Query Security Data Mesh. That means they can pull context from across tools, stitch together evidence, and deliver answers you can act on.
What it does: Finds where a file hash has appeared across your environment.
What you get: Fast visibility into where a file hash has appeared in your environment, enriched with context like first seen, last seen, related assets, and detection history.
Replaces: Manual IOC sweeps and cross-tool hash lookups.
What it does: Surfaces network events for a given IP, asset metadata, who owns it and how it behaves so you can quickly assess exposure, intent, and threat relevance.
What you get: Full picture of traffic patterns, asset links, and threat context.
Replaces: NetFlow queries, WHOIS lookups, and tool-to-tool pivots.
Under The Hood
Each agent runs on the Query Security Data Mesh.
AI-ready
Data
One normalized data payload, structured to enhance LLM performance and accuracy.
No Data Movement
Agents query data where it lives, across EDRs, cloud logs, SIEMs, and vulnerability scanners.
Semantic Understanding
They use a unified schema and context-aware logic to generate precise, valid queries.
Curated Knowledge
Agents reference standards from CISA, STIX, MITRE ATT&CK & NIST to deliver trusted guidance.
It’s like having a team of tireless specialists who already know your data.
Industry Feedback
From Manual Grind to Mission Complete
Security teams waste hours gathering context about what a finding means, who owns the asset, where a hash appeared, whether a CVE matters. That’s time that is better spent on taking action to prevent and defend against threats.
Query Agents eliminate that grind. They pull the right evidence, from the right tools, in real time and dramatically increase the productivity of your team.
- Go from 30-minute triage to instant, evidence-backed summaries
- Investigate threat intel with no copying, pasting, or IOC formatting
- Know which CVEs affect you and how to fix them without digging through scans
- Trace an IP’s behavior and relationships in seconds, not hours
- Enable junior analysts operate like seasoned responders