Supercharge your Splunk
with Query Federated Search
Query is a Splunk App that easily adds data sources to Splunk without increasing ingestion or compute expenses. Your Splunk — but with a lot more data.
Watch the two-minute demo
Why Splunk + Query?
How Splunk with the Query App is more than the sum of it’s parts
All the Data, All in Splunk
Splunk is a powerful technology for ingesting and indexing data and writing detections against that data. But, for various reasons, not all of your security relevant data lives in Splunk, and the data that does requires continuous engineering cycles to maintain. As investigations expand beyond the scope of data visibility in Splunk, analysts must wade through tool consoles upstream. Latency issues arise, eventually turning into budget issues at scale.
Query is a bridge between Splunk and your data, wherever it is stored, making more data accessible and actionable within your Splunk instance. With Federated Search and in-flight data normalization, Query can add additional data to your Splunk reports and rule sets seamlessly. All without pipelining, pre-processing data, or duplicating data. This allows security teams to:
- Rapidly onboard data sources — leave data at the source or store elsewhere, Query does not duplicate or store your data and data does not need to be ingested or stored in Splunk to be used in Splunk.
- Search for relevant data beyond the scope of normal security tools: ERP, HRIS, and business applications.
- Deepen existing ROI on Splunk resources, expanding the power of Splunk across a higher volume of data.
- Deepen existing ROI on other tools and their data by providing easy data access to analysts and operators within the Splunk console.
Choice & Control of Splunk Storage Costs
Security-relevant data volumes continue to increase, with no sign of slowing down. Whether it is expanding costs of ingestion and storage in Splunk, or increasing compute costs in lakes, warehouses and XDRs, the cost of security is steadily increasing too, leading to tradeoffs between data availability, currency, detection efficacy, and the overall effectiveness of your security program.
Query allows data to be searched no matter where it is, without incurring expense for compute, storage or ingestion. Query deconflicts IT spend from achieving security outcomes. This includes:
- Deploying bridges into, and across, all of your data stores: object, lakes, other SIEMs, warehouses, and directly from the source APIs.
- Accessing archived, historical and real-time data – from event logs to CMDB entries to security findings.
- Avoiding vendor lock-ins and accelerating SecOps-related migration and transformation projects by providing federated search access to all relevant data stores.
Accelerate Your Splunk and Your Security Team
When it comes to investigating an incident or threat, analysts, detection engineers, and other operators need access to data – fast. With Query, Splunk becomes the epicenter of your investigation & detection workflows, providing both first party connectors to security-relevant data providers and easy access to dynamic schemas such as those in other Splunk indices, as well as in Snowflake, Google BigQuery and Amazon S3.
With more and more relevant data in your Splunk instance, your detection engineers can interdict distinct threats and tradecraft more quickly, and all other operators can benefit from gaining access to all the relevant data they ever need. Operators can:
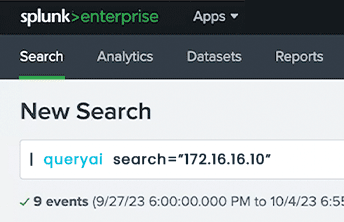
- Use the familiar Splunk interface and search processing language (SPL) as well as all of their existing reports.
- More frequently pivot into follow on searches without having to leave Splunk.
- As new data sources are indicated as relevant to your search, add them on the fly in minutes and get access to the new data in time to support your investigation.
- Reduce analyst fatigue by reducing data hunts and by allowing them to concentrate their entire workflow in Splunk
Getting Started with Splunk + Query
In minutes, start adding new data sources to Splunk with Query
1
Download the App and
Set Up Your Account
Download the app from Splunkbase and define your Organization. Your first Organization is usually your company, but it could also represent a team or other group.
2
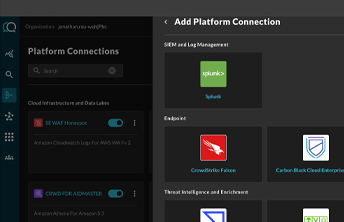
Connect your
Integrations
Set up Integrations, which are connections to data sources. You will need your access credentials, which could be URL, API keys, auth tokens, etc. Check out the available Integrations in the next section.
3
Perform your
first Query!
Start typing using natural language to instantly search across all of your connected integrations!