Quick Links
What is federated search for security?
According to Gartner, “Federated search aggregates the results of a user-initiated search to multiple search engines and presents those results back to the user. Sometimes federated search interweaves the results so that they are compared with each other; sometimes they are just presented next to each other as alternatives.”
(Gartner, 2024, Federated Search para 1)
Basically, federated search means searching multiple sources from one place, like how Google searches different websites throughout the Internet from one search bar.
However, federated search for security must support many distributed data sources and formats, searching using different languages and syntaxes, then normalizing the results.
How can federated search improve security operations?
While federated search has existed for decades, the cybersecurity market only recently started to adopt its capabilities for security use cases. With the volume and variety of data that security teams need to access and analyze daily, it’s easy to see how federated search can provide strong value. When done right, this capability can allow security teams to bridge the data silos and investigate across toolsets that reside in their cloud, SaaS, and on-premises environments.
With federated search, you can make a single query request and get answers from all data sources, such as security technologies, SIEMs, data stored in Amazon S3 buckets, Active Directory, human resource systems, Windows event logs, and more. The federated search then aggregates the results and presents the unified information to the security analyst. This prevents having to pivot and manually login to many different applications to investigate.
Federated Search is one search box that allows you to:
- Search everywhere at once – so you don’t have to know where to search, gain access to search, and know how to search.
- Eliminate repetitive searches – so you don’t have to cut and paste the same search into many systems.
- Gain complete visibility – so you can see the complete picture from your data, including graphical data detailing the relationships of events within your system.
- Get answers to your questions – so you can significantly reduce investigation time.
Different approaches to federated search
Federated search functionality in the cybersecurity industry is only starting to reach its full potential. In its current applications, the market is seeing two approaches to federated search: single vendor and open federated search models.
Single Vendor, or
Closed Federated Search
As the name implies, single vendor federated search allows security teams to execute a unified search across a single vendor’s toolsets. It is most often seen today in SIEM solutions to create a search bridge between an organization’s cloud and on-premises instances of the vendor’s products. This enables security teams to search on security event data across their cloud-to-cloud, on-premises-to-cloud, and on-premises-to-on-premises instances of that single vendor’s solution.
While a helpful start to federated search, this approach means security teams still must pivot to individually search in other relevant environments, such as AWS and Elastic, and in other vendor data sources to reach an outcome for each investigation and incident response effort. Single vendor federated search also relies on the traditional approach of moving and centralizing the organization’s data within that one vendor’s solutions.
Open Federated Search
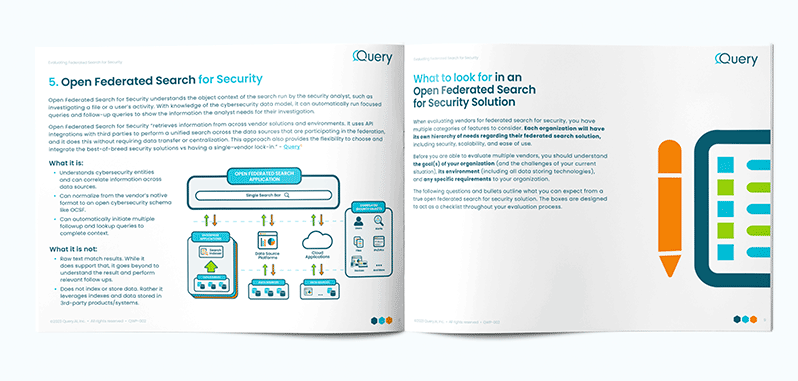
Open federated search retrieves information from across vendor solutions and environments. It uses API integrations with third parties to perform a unified search across the data sources that are participating in the federation, and it does this without requiring data transfer or centralization. This approach also provides the flexibility to choose and integrate the best-of-breed security solutions vs having a single-vendor lock-in.
This approach expands the flexibility of security teams to access their siloed data sources from across cloud, SaaS applications, and on-premises environments, enabling them to eliminate pivots and individual searches across data silos so that an organization’s security operations can efficiently and rapidly get from the initial investigation question to a high-confidence incident response outcome.
Let’s look at some
common Use Cases
Security Investigations
If an unsuspecting employee falls for a phishing email and clicks on the malicious link that steals her credentials, the SIEM will sound the alarm that there was a suspicious Office 365 login. However, this doesn’t tell the analyst anything about the user or that the origin of the suspicious login started from a phishing email, much less if any other employees received the same phishing email.
This typically is when an analyst begins pivoting in the investigation with searches in the Active Directory system to identify the user and original machine that received the phishing email. With open federated search, security teams can search on the suspicious login details and simultaneously access Active Directory to uncover the user associated with the event and see how many and which other users also have attributes of the phishing email on their machines.
Check out our Solution: Security Investigations — Accelerating Investigations With Expanding Data Visibility Using Query Federated Search
Threat Hunting
When there’s an alert on a malicious IP, analysts first search in the SIEM or other central logging system. From there, they need a lot of additional information from other system logs that are not centralized in the SIEM (e.g., threat intel, EDR context, DLP, asset management, etc.).
Instead of having to log in to each system separately to continue the investigation, the open federated search model lets an analyst run the query across all systems, which gives security teams instant and unified answers to the investigation questions. This allows security operations teams to search fluidly across security events and the operations data, such as Active Directory, human resource systems, asset management, and ticketing systems to unveil the full investigative story.
The result is a complete view of the decentralized environment and its wide-ranging data sources that the security team needs to access to quickly and efficiently complete investigation and incident response efforts.
Check out our Solution: Threat Hunting — Threat Hunting With Query Federated Search
Incident Response
When there is an incident, things can get stressful. Teams need answers fast. The actions described above for security investigations and threat hunting are useful for IR. Additionally, historical data becomes a key element in understanding the full scope and impact of the incident.
Open federated search enables the responder to answer questions across many distributed data sources about what is happening right now, what happened in the past, and what happened in between. This ability to follow the trail across time is critical to understanding the full story, but, without the ability to quickly search across many data sources, it is incredibly time-consuming to piece together manually. Investigations often require access to expanded data sets, and open federated search can be used to expand the visibility of the responding team quickly, all from one search box, without the need to provision and manage access for many responders.
Incident Response is a team sport, so the ability to share findings with others is also a key element of open federated search. When incident response moves into the contain and eradicate phases, the ability to share findings from the investigation in the tools teams are already using, like ticket systems and chatops, can accelerate everything.
Check out our Solution: Incident Response — Exponentially Increase Incident Response Efficiency with Query Federated Search
Benefits of open federated search
Security teams need a lot of information to move from the security alert phase to the final outcome of an investigation. Just like a good investigative journalist needs to dig into the details of a story, security practitioners need to know a lot more than the high-level “what” information they get from a security alert.
In short, they need the full context on the who, what, when, where, why, and how of a security situation to gain a complete understanding. This information comes from a variety of siloed data sources across the environment. Open federated search allows security teams to achieve this goal of gaining context.
Query Federated Search
Query aims to deliver visibility into all the data a security team could ever need, unlocking access to data at the source and in your data lakes, creating many opportunities for more nimble and cost efficient data storage architectures.
Our customers are using Query to expand visibility for security investigations, threat hunting, and incident response, and they are already drastically reducing the time and complexity of repetitive search tasks.