The best defense against a bad guy with AI is a good guy with AI.
That reads like a bumper sticker, but it’s a front-line reality in modern cybersecurity programs. AI has pushed us into a phase shift, one where the barrier to entry is falling fast, and the ceiling for impact is rising even faster. What used to require deep expertise and time now takes prompts and minutes.
Attackers have already adopted AI, and the impact is just starting. Many successful exploits led by humans are opportunistic. Attackers get in through a weak link, then evaluate the potential value of the environment and the targets. The process (think of it as the business side of hacking) requires significant skill, judgment, and time to do well. It’s where attackers go from agent of destruction to skilled intelligence analysts by researching org charts, roles, intellectual property, and infrastructures, to determine how to profit, and therefore, what to do next. In other words, it’s the strategic layer of hacking and AI is making it faster, more scalable, and dangerously efficient.
We’re not talking about one-off hacks. We’re talking about continuous, adaptive, industrialized exploitation.
Let’s break it down.
High-Value Targeting Agents
AI agents are already capable of scouring public repositories for misconfiguration, generating working exploits based on vague vulnerability reports, and guiding attackers step-by-step through compromise paths. Script kiddie zombies are coming: attackers with little to no technical foundation using AI agents to automate the entire cyber kill chain from reconnaissance through to exfiltration or other actions on the objective. But even more troubling is what advanced threat actors can now achieve with AI-driven scale, speed, and creativity.
Imagine a High-Value Targeting Agent guiding the attacker. Once in an environment, possibly through phishing or an exploit, it runs a cascade of classification models: what system am I on? Who owns the system? What data is here? What are the connected assets?
The agent provides context and guidance through each step by coordinating efforts and guiding the exploitation path.
Is it a test environment? Move on. Is it a senior executive’s device tied to CRM, payroll, and legal systems? Escalate. Persist. Exfiltrate.
With AI, this isn’t a manual process. It is scalable, repeatable, and ruthlessly efficient.
Real-Time Compromise Copilots
Traditionally, lateral movement requires human creativity. You have to understand relationships between identities, privileges, network topology, and tools. Even with good red team skills, it’s slow work. AI changes that.
Attackers are already building compromise pathfinding agents, AI copilots that use discovery data (endpoint inventory, identity graphs, application logs) to generate step-by-step breach pathways in real time. They adapt as they go, rerouting if something breaks, like a video game quest marker, to the fastest compromise path – just follow the red compass marker.
AI automates the entire kill chain, from initial access to exfiltration, guiding attacks in real time and aligning them with frameworks like MITRE ATT&CK. What was once a defensive model becomes a dynamic offensive playbook. It won’t be long before Procedures and Threat Groups in ATT&CK become filled with AI-specific tooling and threat actors.
This isn’t about brute force through numbers. It’s guided, intelligent intrusion.
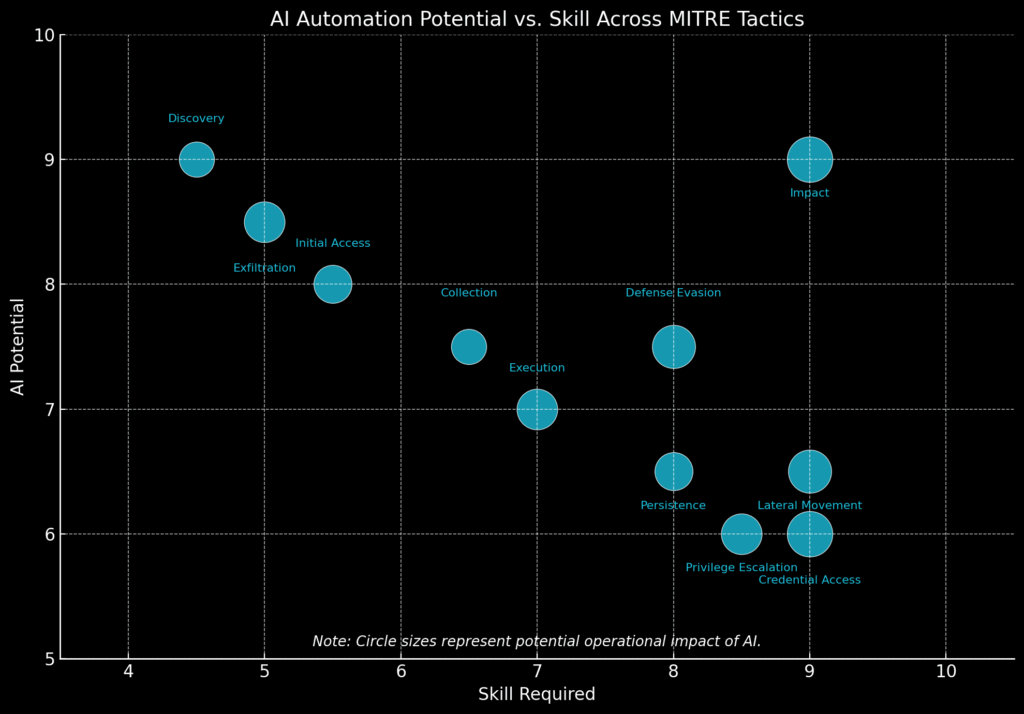
Exploit Chaining and Creation at Machine Speed
Exploit chaining is a known technique. Combine two medium-severity bugs, and you can sometimes break open an environment, if you can link a successful path together. AI turns this from art to science.
With the ability to simulate environments, reason through documentation, and reference large corpora of known CVEs and patches, AI agents can chain vulnerabilities faster and more comprehensively than any red team. They can map these chains to specific configurations in an enterprise, adapting them on the fly, and generating working proof-of-concepts in minutes.
And with the right model fine-tuning, they won’t just use known exploits – they’ll create new ones. You have likely heard of LOLBAS – Living Off The Land Binaries, Scripts and Libraries. Malicious AI agents will be able to manufacture exploits and defense evasion tradecraft in place with any number of LOLBAS it has access to.
So that’s the threat landscape. What’s the counterbalance?
AI for Defenders
Here’s the good news: defenders are wielding AI, too. And when it’s integrated with real-time data and used with purpose, it doesn’t just help teams keep up, it gives them the upper hand.
At Query, we’re building the kind of tooling security teams need in this new environment. Our AI-powered Copilot sits on top of a Federated Search engine that gives analysts real-time access to data across their cloud infrastructure, SaaS, identity, and endpoint systems, without pipelining or ETL. It translates questions into structured searches, normalizes the data, and returns results with context.
This isn’t theoretical. We’re seeing teams use Copilot to:
- Summarize threat investigations across 12+ tools.
- Identify hidden lateral movement paths.
- Automate answers to complex audit and IR questions.
- Build dynamic security narratives that combine identity, asset, and alert data.
- Receive detailed prioritization and remediation guidance.
The result? Security teams move faster, understand more, and act with confidence, without chasing logs across browser tabs or waiting for new data pipelines to be built.
The AI Defender Advantage Is Real
We’re in a cyber arms race. But this time, the arms are intelligent, adaptive, and invisible.
Attackers have AI. But defenders have AI plus something better: access, context, and the power to combine human judgment with machine precision.
Over the past few months, a new name has been dominating the HackerOne leaderboards: XBOW. Fast. Consistent. Lethal. This top-performing security researcher isn’t a person. XBOW is AI, an autonomous vulnerability hunter using machine intelligence to find flaws faster than most humans ever could.
When AI copilots are wired into all your data, and designed to assist – not replace – your security teams, the defender advantage is real. With every search, investigation, and response, the good guys get faster. This is how we will achieve a strategic victory, and break out of the attritional and reactive cyber defender-attacker paradigm.
Because in the phase we’re now entering, the best defense against a bad guy with AI…is a good guy with more data to enable even better AI.