Complexity is the enemy of modern Security Operations (SecOps). Everyday, new product categories are born and with it they bring more and more datasets, some of them are very pertinent and some of them are duplicative. Data volumes continue to grow even from incumbent tools, and security teams are stuck holding the bag – often with legacy tech that cannot support this new Petabyte-scale reality.
Teams are dealing with sprawling ecosystems of agents (the real kind, not AI), consoles, data formats, and tools. The result? Missing data, increased costs, and painful investigations. When you partner this with legacy SIEM, you have more problems that continue to exacerbate: nearly impossible data governance challenges, being forced to prune back source ingestion, which ultimately negatively impact security outcomes.
Take heed of my words dear reader, there is a smarter way forward.
Query Federated Security and Cribl’s observability pipeline suite form a modular, interoperable architecture that delivers real-time visibility, flexibility, and cost efficiency. Whether you’re trying to search across siloed datasets, transform high-velocity telemetry at the edge, or migrate off of your legacy SIEM; this combination offers a future-proof foundation for security operations.
Cribl + Query: What Each Tool Brings
Cribl Edge: Host-Based Data Collection & Routing
Cribl Edge runs directly on the host or nearby infrastructure to collect logs and metrics. Think of JAMF or Microsoft Intune-managed MacBooks and Windows endpoints: Cribl Edge can capture telemetry before it’s even aggregated. This is particularly valuable when working with ephemeral assets like VDI environments or roaming devices. Host-based telemetry is some of the richest data for detections and triage use cases, be it Windows Event Logs, Kubernetes control plane logs, or otherwise. Cribl Edge provides a great way to collect, collate, pre-process, and move it where you need it.
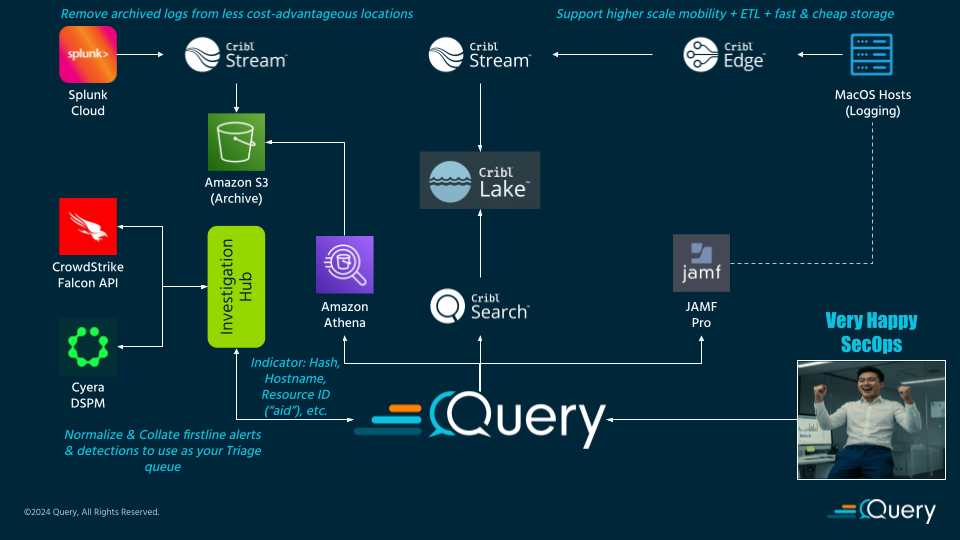
Use Case: Cribl Edge is deployed across remote developer laptops managed with JAMF. It forwards enriched endpoint logs to Cribl Lake (via Cribl Stream) for retention, while also using Cribl Stream to move archived host logs to S3 from Splunk. Query provides Connectors to both Cribl Search, JAMF Pro, and Amazon Athena, allowing threat hunters and triage analysts to gather all of the context on specific hosts for developers or VIPs implicated in firstline detections from other tools such as EDR or DSPM.
With Query Federated Security, none of the data is moved or duplicated, and it is all normalized just-in-time into OCSF to provide a common data format for quicker filtering and pivoting. The Investigation Hub console will collect all alerts, detections, incidents, and other “event” data and normalize them to appropriate Findings-type Event Classes such as Detection Finding and Data Security Finding.
Cribl Stream: Data Shaping and Optimization
Cribl Stream enables transformation, enrichment, and intelligent routing of high-volume telemetry. Cribl Stream integrates in a “push” or “pull” mechanism depending on the data sources. You can move findings from Wiz CNAPP, pull events from TCP or UDP streams (such as from Cribl Edge), or move data from Splunk or Amazon S3. Using Cribl CoPilot you can accelerate the authoring of processing and data transformation to prune and normalize datasets to improve its performance, relevancy, and utility to security operations use cases.
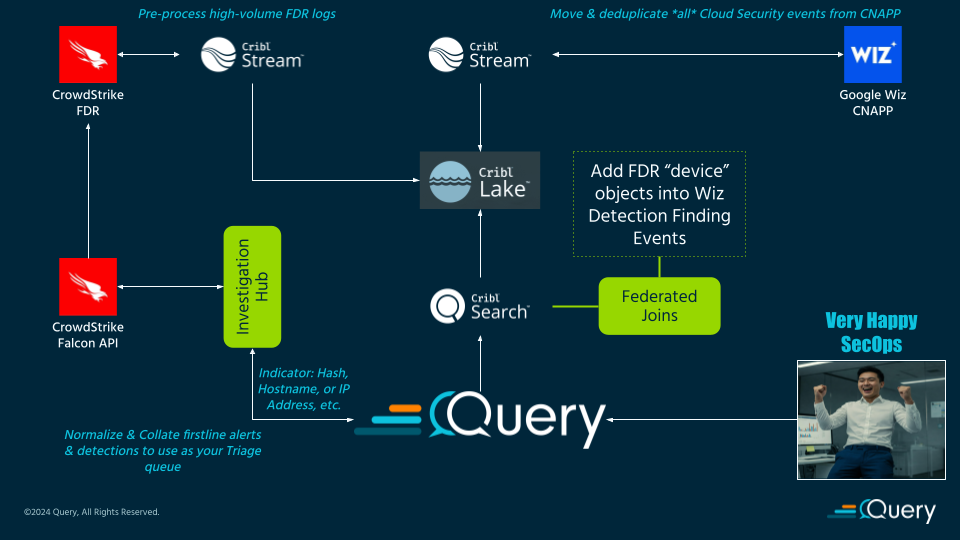
Use Case: Security engineers create a pipeline in Cribl Stream that ingests cloud security findings from Wiz, and deep EDR telemetry from CrowdStrike Falcon Data Replicator (FDR). In the Query console, users can set up Federated Joins that interjoin the host-based logs, the Wiz findings, and FDR findings to simplify threat hunts and triage playbooks by defining it with a Saved Search. Like the other use case, Investigation Hub is used to collect firstline tool alerts, the Federated Joins provide a richer context than collating disparate sources, even if they are similarly normalized.
Cribl Search & Lake: Search + Store, Modularly
Cribl Search is a KQL-based search interface that can search several dozen sources, but optimized to query data in Cribl Lake or Lakehouse without moving it. While its federated capabilities are limited, adding Query’s Cribl Search connector enables analysts to query data at rest in Cribl Lake alongside live feeds from other platforms. Using Lake to store the data in Parquet format, or using Lakehouse to accelerate certain datasets, along with Search can accelerate threat hunts and analytics use cases.
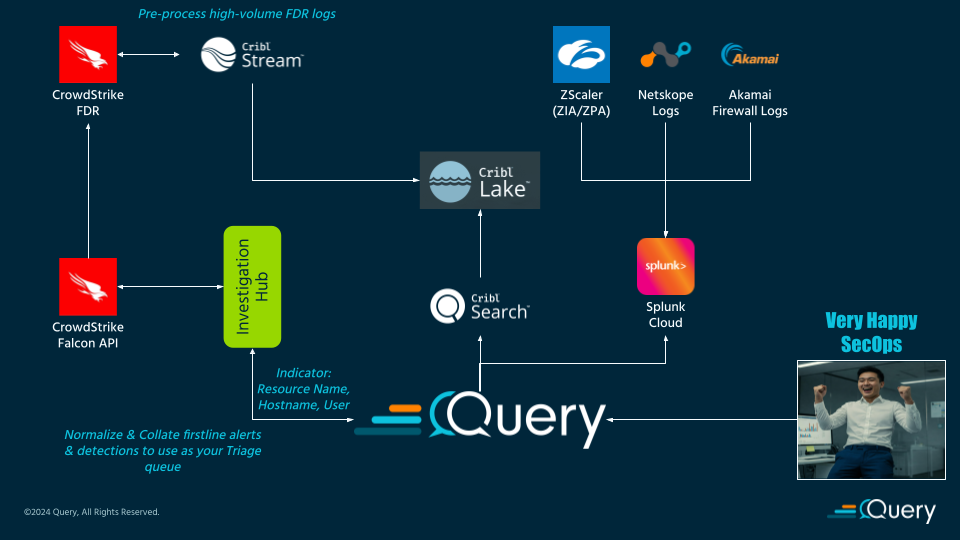
Use Case: A security team stores CrowdStrike Falcon Data Replicator telemetry and Windows Event Logs in Cribl Lake (via Cribl Stream and Edge, respectively). During an incident, analysts use Query to simultaneously search that lake and current indexes in Splunk (i.e., Netskope, ZScaler, and/or Akamai logs) to identify lateral movement paths or provide context onto the full flow of data as it passes through several device-, identity- and network-boundaries.
Query Federated Security: Unify Access, Accelerate Detection
Query provides the connective tissue: a federated security platform that connects directly to disparate systems and storage formats. With Query, your data is never moved again or duplicated into a backend, once you move it with Cribl it doesn’t move again unless you want it to. Query automatically normalizes all search results in the Open Cybersecurity Schema Framework (OCSF) at the time of search, allowing analysts to access dozens or hundreds of different data sources in the same exact way, OCSF becoming your lingua franca both for search and filtering.
With Federated Joins, instead of collating different OCSF event classes in the results, you enrich the records in-situ allowing you to dynamically inject Cyber Threat Intelligence or OSINT enrichment into your records. You can add detailed host data from JAMF Pro or CrowdStrike Falcon into your raw Windows Event Logs, or add user inventory data into authentication logs.
Using the various Query Co-Pilots you can:
- Automatically map your raw downstream datasets – in S3, Snowflake, BigQuery, or Cribl Lake (via Cribl Search) – into OCSF.
- Automatically extract asset data, IOCs, or summarize findings and enrich findings with MITRE ATT&CK mappings and NIST CSF controls per-finding or for a group of findings.
- Use the Federated Search Query Language (FSQL) Agentic workflow and MCP server to build extremely detailed detections, and push them to other platforms or save the searches into the Query console.
With Cribl and Query Federated, you can simplify and right-size your security stack. Put the data in the places that make the most sense, such as leaving your M365 E5 datasets in Microsoft Sentinel, moving host based logs from Cribl Edge into Cribl Lake, and opting out of moving datasets like alerts or detections firing in CrowdStrike Falcon and unifying access with Query.
Why CISOs and Architects Are Choosing This Model
For CISOs and architects, the strategic pressure is high: enable agility, reduce costs, avoid lock-in, and support compliance while delivering top-tier security outcomes. The Query + Cribl model meets this challenge with a federated, modular approach that is built for flexibility and resilience.
- No Vendor Lock-In: Keep your data where you want it, in formats you control.
- Cost Reduction: Avoid duplicating ingestion into expensive SIEMs. Use Query for federated detection and search and Cribl for intelligent routing.
- Detection Agility: Enable your detection engineers to iterate faster with real-time data access, directly on the data, without requiring movement to specific data stores which introduce latency.
- Open, Schema-Aligned: Built on OCSF, allowing you to create IR playbooks, detections, analytics, ad-hoc search, and ML feature extraction all in the same way against the same schemas.
- AI-Ready: With the same open schema – and existing Query Federated Security Co-Pilots, Agents, and Model Context Protocol (MCP) – you can develop security-specific AI workloads using federated search and just-in-time normalization to extract the most relevant context for your LLMs.
In short, this architectural pattern is built for the future, where analytics, detection, and compliance are distributed and continuous. It allows security leaders to take control of their data strategies while empowering teams to deliver better security outcomes with lower operational burden.
This model lets you optimize for control, scale, and security outcomes on your terms, not your vendors’.
Final Thoughts
Security teams don’t need more point solutions. They need composable platforms that interoperate. With Cribl handling data movement and transformation and Query enabling true Federated Security, organizations can finally simplify, modernize, and accelerate their security operations, and all other organization-wide security tasks.
This is how SecDataOps should work.
If you want to explore this architecture in action, the Query team offers hands-on support to help you get started. You can learn from real-world implementations, customer stories, and success frameworks by requesting a SecDataOps Workshop to assess your current architecture and identify opportunities for transformation.
Already ready to see it live? Kick off a Proof of Concept (POC) by booking a personalized demo with our team. Experience firsthand how federated security can unify your tooling, accelerate investigations, and reduce operational overhead.
Contact our team to request a workshop or schedule your demo.
Stay Dangerous.

