What would life be without OpenSSL, can we even imagine one!
By definition, OpenSSL is an open-source crypto library implementing SSL and TLS protocol RFCs. It is quite easy to use OpenSSL for several routine tasks that we need in the everyday usage of crypto, and other daily need-to-knows of programmers. By understanding command-line options, you can run them on your Windows shell or Linux command line. (Just make sure to have utility OpenSSL installed and available.) Nowadays, many Linux distributions come with OpenSSL pre-installed.

Any guesses on what this is? Trying zooming into the text in the image.
The manual of OpenSSL lists the following capabilities:
- Creation and management of private keys, public keys and parameters
- Public key cryptographic operations
- Creation of X.509 certificates, CSRs and CRLs
- Calculation of Message Digests
- Encryption and Decryption with Ciphers
- SSL/TLS Client and Server Tests
- Handling of S/MIME signed or encrypted mail
- Time Stamp requests, generation and verification
But beyond above, OpenSSL is capable of doing much more. For this article, we are only going to scratch the surface and check out how OpenSSL can help us complete simple tasks. OpenSSL is so versatile, powerful, and big that one article is not enough, so let’s get started.
The capabilities of OpenSSL range from cryptography to a toolkit for hackers, but that does not mean analysts and sys-admins cannot benefit from its power. All you need is a little bit of command-line knowledge of Linux shell. We will perform some common tasks later in this article, but first, let’s look at a full list of command families:
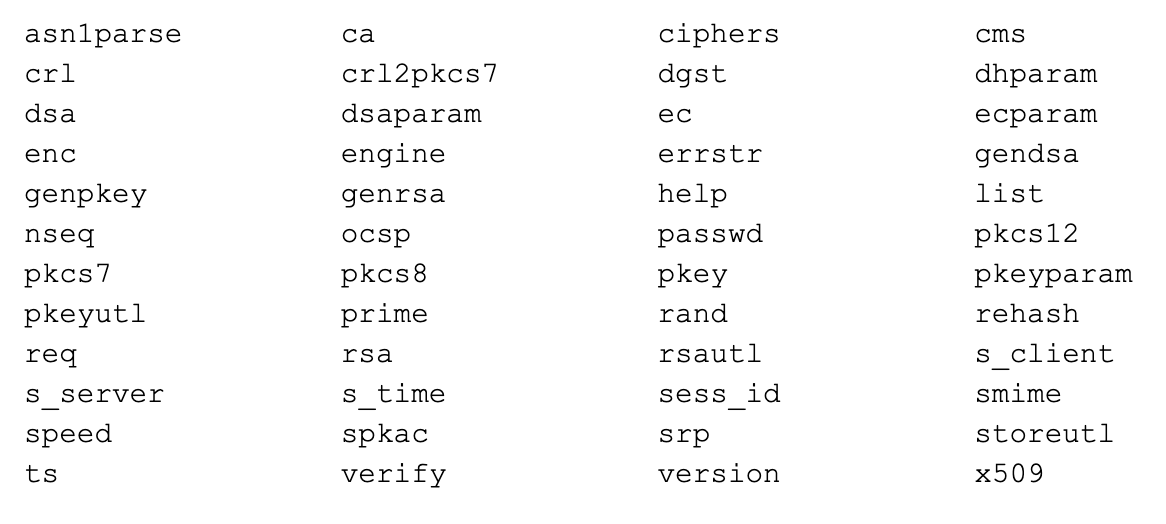
Message Digest commands (see the `<em>dgst</em>‘ command for more details)

Cipher commands (see the `enc‘ command for more details)

Common Uses
You have a really excellent ssl/tls client and server test application in OpenSSL.
<em>$ openssl s_client</em> and $ openssl s_server
They are the test TLS client and server applications which can be incredibly useful for a wide variety of testing and diagnostic purposes for programmers, security analysts or sys admins.
Here are some test invocations:
$ openssl s_client -connect <a href="http://www.google.com:443/">www.google.com:443</a>
Here is the sample output:
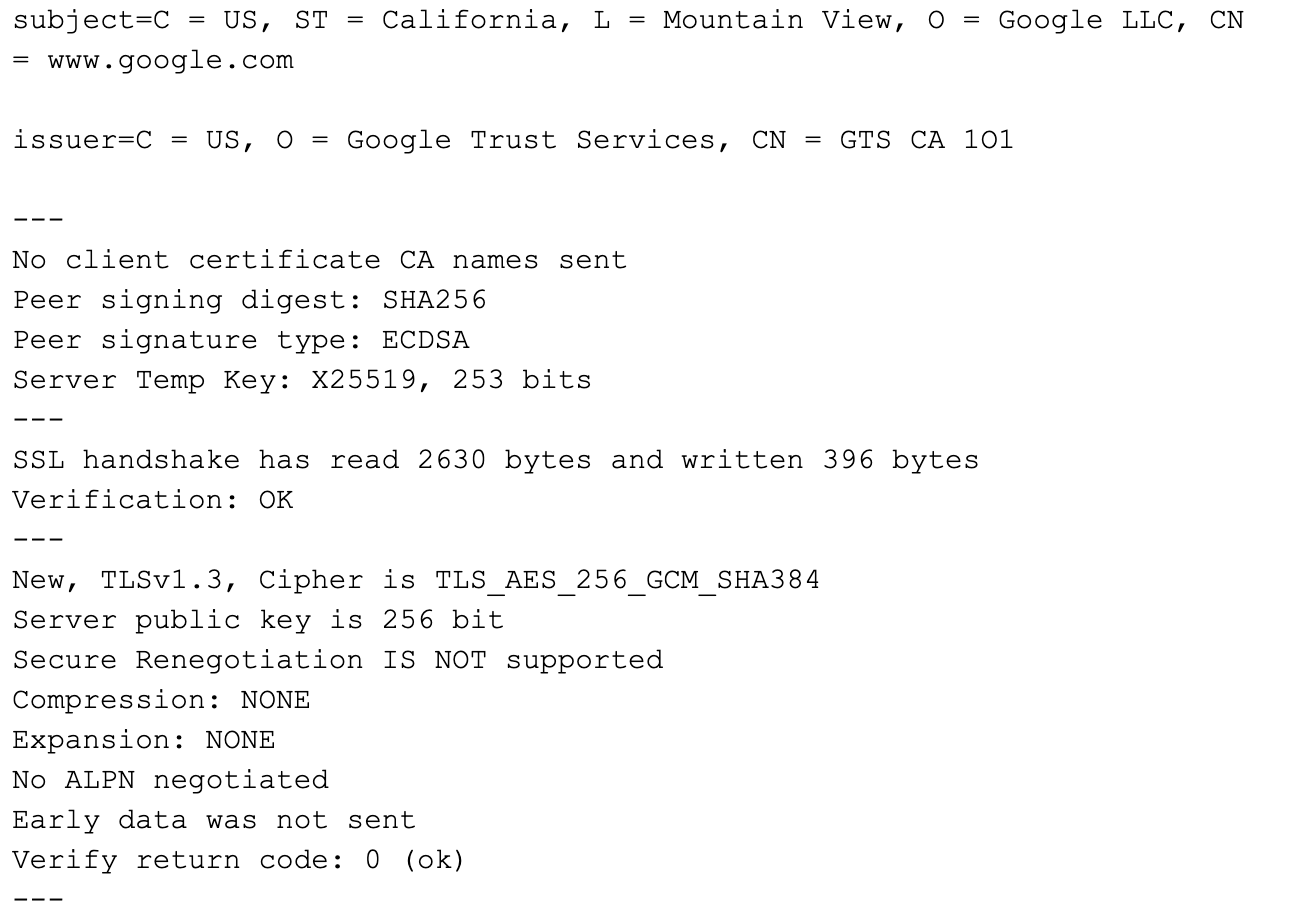
You can do a lot of stuff with these SSL wrappers as most protocols are SSL enabled on the Internet today. In addition to checking for the cipher suites that are negotiated in an SSL connection, you can find out certificate’s trust hierarchy or expiry date and so on.
Apropos of this, if you wish to simply SSL-enable a particular insecure app, you have a tool called stunnel.
Now let us do some simple encryption and decryption with OpenSSL.
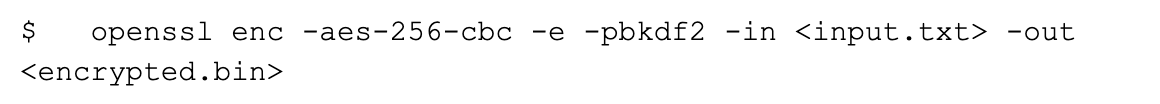
To inspect it:

Then you can use the encrypted file or send it and then finally to decrypt it:
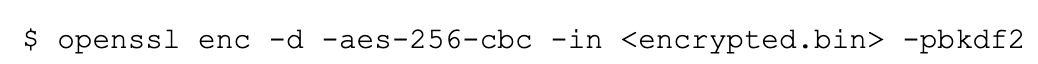
You can start by computing the hash values of big files or simple strings: userid and password colon separated for HTTP digest authentication.
To do simple cipher manipulations like this, we have another utility in the UNIX universe called GnuPG.
Then there is also X.509 certificate manipulation, including generation, checking, computing the hash, generating RSA keypairs, and converting certificates between PEM, DER, and PKCS12 formats.
Conclusion
The capabilities of OpenSSL range from cryptography to a toolkit for hackers, but that does not mean analysts and sys-admins cannot benefit from its power. In this article we scratched the surface of possibilities. What benefits do you see from OpenSSL?
Did you enjoy this content? Follow our linkedin page!


