Continuing with our fast pace of innovation, I am excited to announce the release of Query Splunk App 2.8, now available via Splunkbase! This release brings a host of capabilities for Splunk users to realize maximum value from the Query Security Data Mesh. Both new users and power users get more value and an easy, seamless experience.
Before we dig into the new features, a quick background on Query Splunk App…
What is the Query Splunk App
The Query Splunk App enables you to add access to any connected data source into Splunk – without increasing ingestion or compute expenses. The Query Security Data Mesh expands Splunk’s reach to all the data you need, including from data lakes, warehouses, object storage, or any other connected source with security-relevant and observability data to support your Security Data Operations use cases, and more. The Splunk app deploys Query capabilities into Splunk, so you can search data sources not ingested into Splunk, see the results as part of your Splunk console search results, and trigger detections without centralizing data. To learn more about the Query Splunk App, go here.
What’s New in Version 2.8
Improved Streaming, Scale and Performance
Users will notice faster and snappier loading of results in their searches, especially when they have tens of thousands of results. This is because of more intelligent and efficient batching and rendering of results in the app. Also, the table in our federated search view now supports streamed loading of results coming from parallel queries.
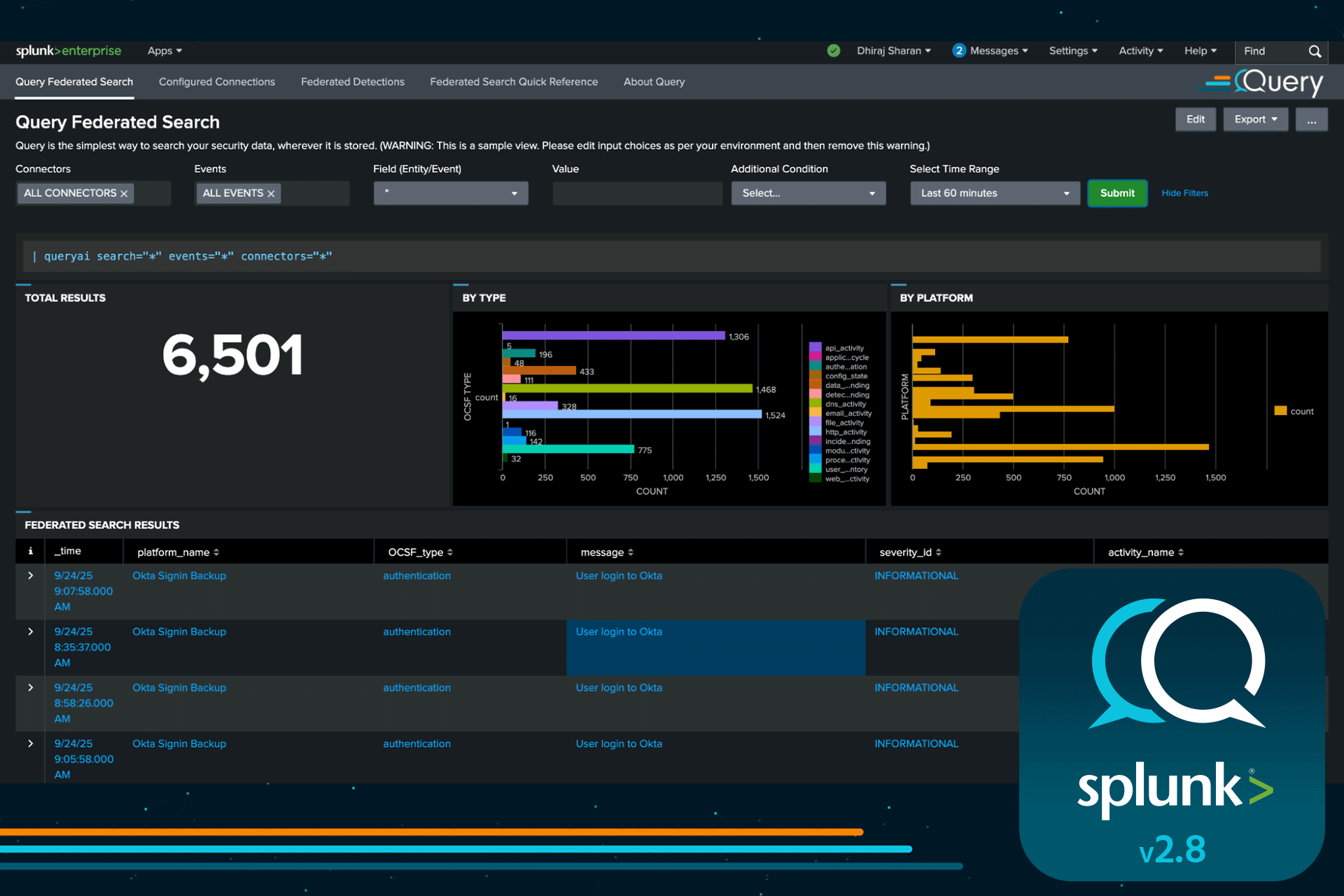
New Federated Search View
For the users that want an interactive UI instead of our | queryai SPL search command, we now have a Federated Search View that gives you the ease and flexibility to operate within the Splunk UI and run your searches. The view also lets you drill down and use the | queryai SPL extension to put you on-way to becoming a power user.
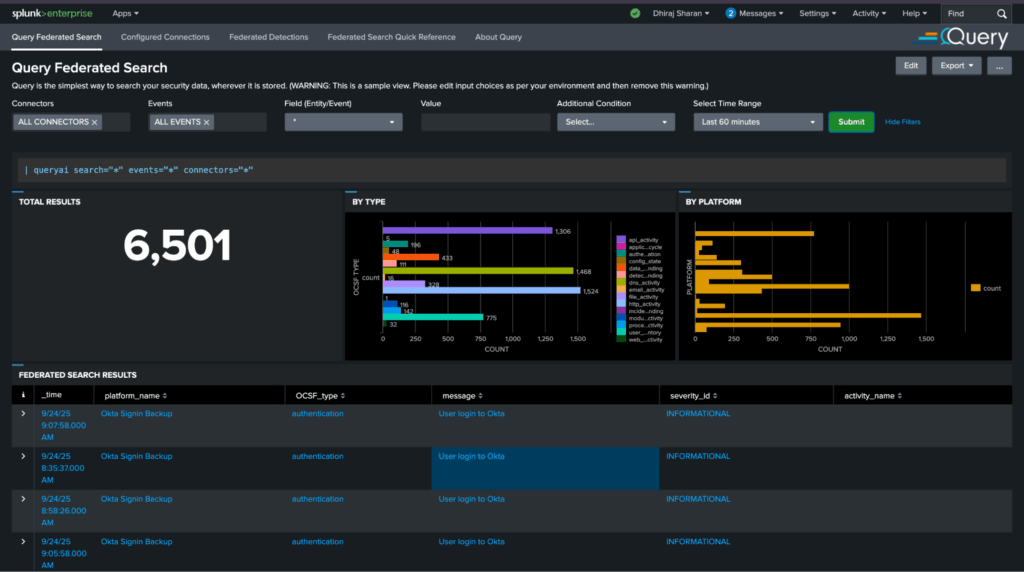
Run FSQL (Federated Search Query Language) from your SPL Pipeline
Federated Search Query Language (FSQL) is a powerful and intuitive query language designed specifically for security analysts and threat hunters to run parallel searches across multiple security data sources through a unified interface.
In this release, we now support FSQL directly from Splunk Search via the | fsql command. For example, here is how you would query authentication failures from your Okta connector:
| fsql QUERY authentication.** WITH authentication.status_id = FAILURE FROM 'Okta Signin Backup'To learn more about FSQL, please see our Introduction to FSQL. SPL users can also refer to From SPL to FSQL: A Security Analyst’s Guide.
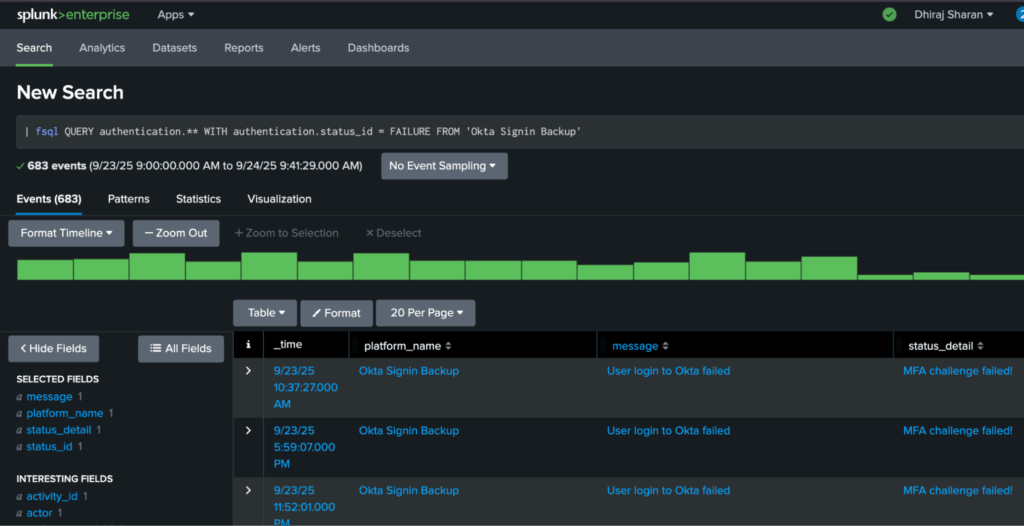
More Powerful Compound Searching
Until now, users have had to refer to OCSF events’ schema field hierarchy (available here) to write conditions. In this release, we now support writing conditions directly by using entities. For example, in this query, you can search for all events having the given hostname or IP in their hierarchy for fields that have been mapped to entities.
| queryai search="hostname=querylab-engg12 OR ip=172.16.119.86"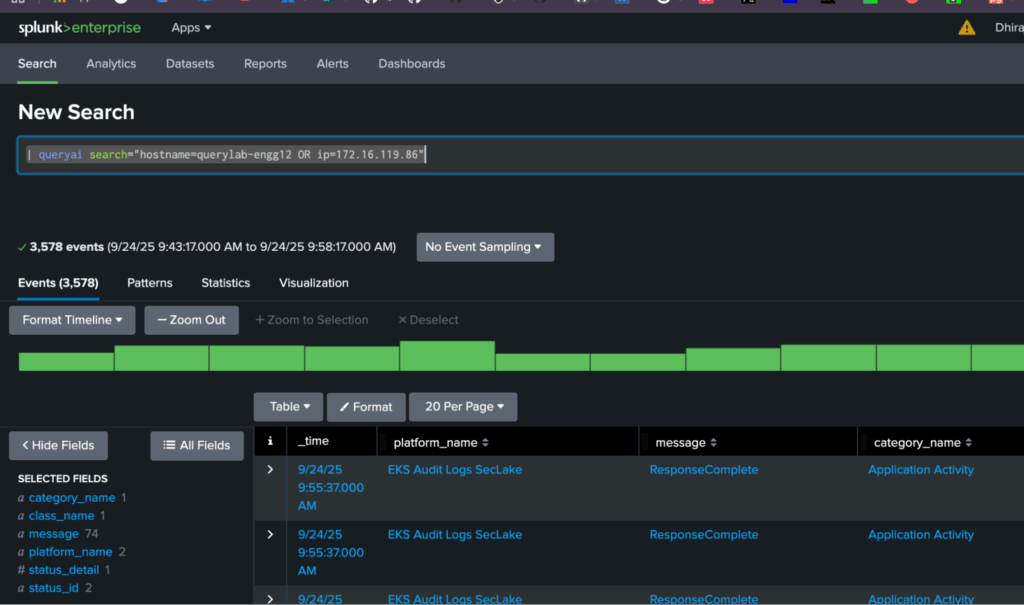
Easily Search across common attributes of event classes
Different event classes (see here) are derived from a common Base Event whose fields are common across all event classes. Now you can search across different classes by putting conditions on the base event fields. For example, look for high severity denied actions this way:
| queryai search="severity_id=HIGH AND action_id=DENIED"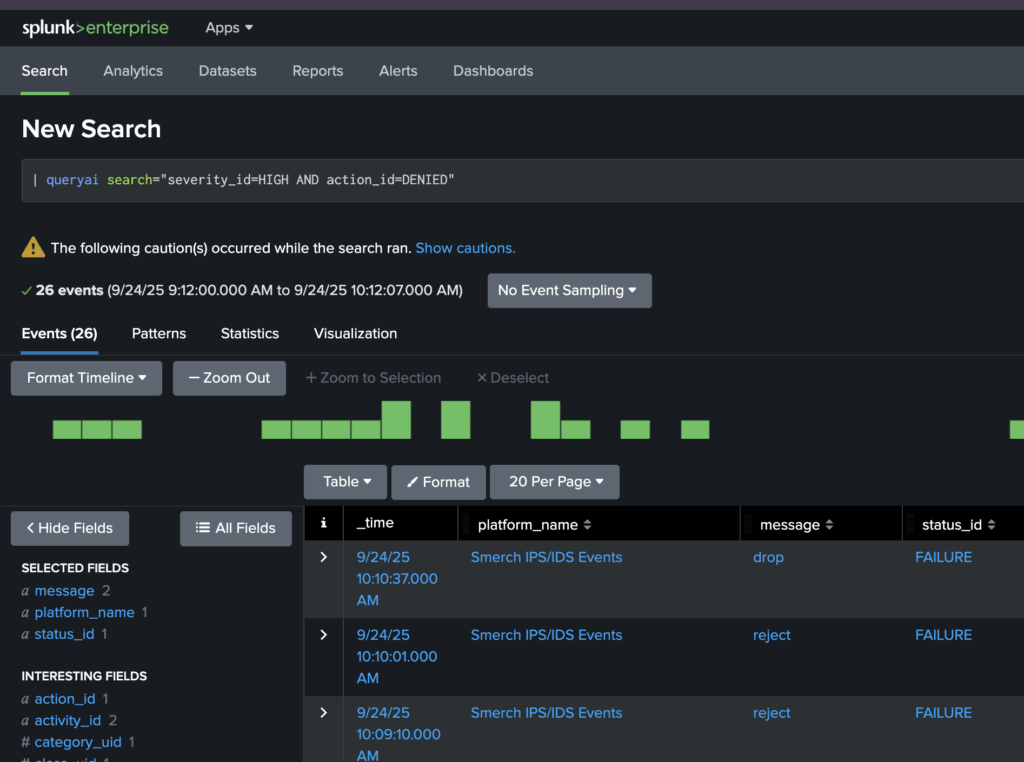
Explore data easily with star (*) searches
Analysts often like to investigate by starting with the haystack, i.e. everything (*), and then filtering down to get to the needles. In this release, we now support star searches in all the places where it is relevant, for example:
Search Everything:
| queryai search=*
| queryai events=*
| queryai search=* events=* connectors=*Search All API Activity:
| queryai search="api_activity=*"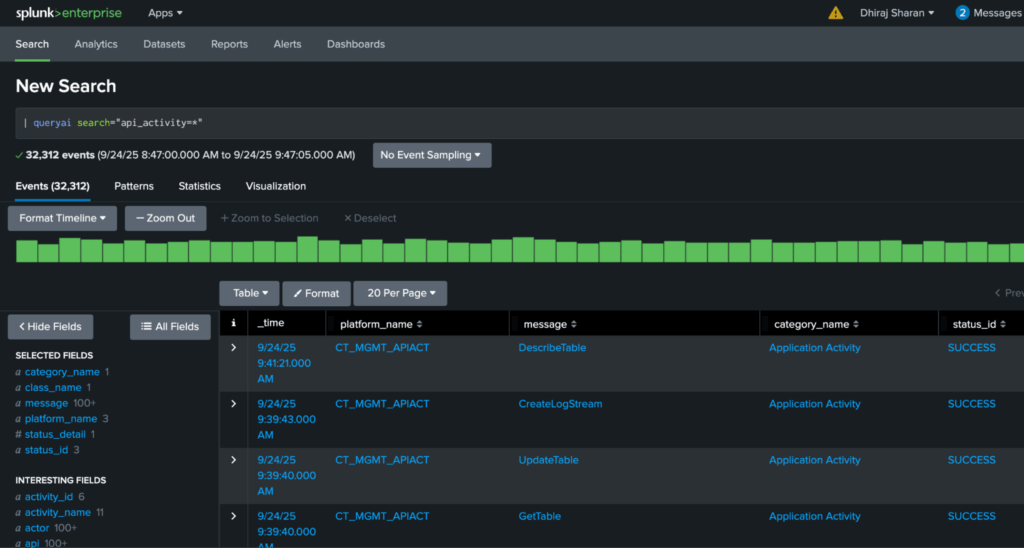
Improved IN operator with wildcard support
Previously the IN operator was only supported with equality and without wildcards. Now we have made it more flexible to cover criteria for starts-with, end-with, or contains, by allowing starred values. So for example, you can search for these DNS Activity hostname patterns this way:
| queryai search="dns_activity.query.hostname IN ('*.ngrok.com', '*.ngrok.io', 'ngrok.*.tunnel.com', 'korgn.*.lennut.com')"The above conditions enable you to detect NGrok proxy usage. Using IN operator conditions this way is immensely flexible, succinct, and effective.
How to try Query Splunk App
With the above improvements, this new Query Splunk App release is a major step forward. The release is now available on Splunkbase for all environments – Splunk Enterprise, Splunk Cloud Victoria, and Splunk Cloud Classic.
Access the app here and view our product documentation here. Contact us for help setting it up.