For modern security and risk management teams, compliance is no longer a quarterly checklist—it’s a continuous imperative. From HIPAA to PCI DSS, GDPR to SOX, security and compliance teams come under pressure to quickly produce evidence, prove controls are in place, and trace access or actions across their sprawling data.
But here’s the dirty little secret: most organizations struggle to get a complete picture of the data they already have. Security-relevant logs and events are often not present in the SIEM for reasons like cost, scale/performance practicalities, data siloes, and more. Data stays scattered across SIEM, EDR, S3 buckets, multiple cloud provider accounts, SaaS platforms, and data lakes. Investigating even a single user action often requires jumping between 5–10 tools.
Now imagine doing that under the pressure of an audit.
Enter: Query Federated Search. It’s your secret weapon for proving compliance across all environments without duplicating data or waiting on data engineering teams.
Key compliance clauses that need Federated Search across distributed data
Let’s take some specific examples. Here are just a few clauses from real-world compliance mandates that demand cross-environment data visibility:
NIST SP 800-53 Rev. 5 – AU-6 (Audit Record, Review, Analysis, and Reporting)
“Review and analyze system audit records for indications of inappropriate or unusual activity and the potential impact of the inappropriate or unusual activity”
(https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf)
You need to show a comprehensive audit review across your security-relevant data.
Federated Search enables you to investigate audit logs from SaaS apps, network infrastructure, cloud logs, identity and user activity data—normalizing them into a single timeline for reporting or presentation to auditors.
FedRAMP – Control AC-6 (Least Privilege)
“Employ the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) that are necessary to accomplish assigned organizational tasks.”
(https://www.fedramp.gov/assets/resources/documents/FedRAMP_Security_Controls_Baseline.xlsx)
An example of what you need to verify, is whether a user was granted excessive privileges or accessed restricted services.
Federated Search lets you correlate IAM logs from AWS, Entra ID, Okta, and more, to quickly demonstrate adherence to least privilege policies.
SOC 2 TSC CC7.2 – Monitoring for Security Events
“The entity monitors system components and the operation of those components for anomalies that are indicative of malicious acts, natural disasters, and errors affecting the entity’s ability to meet its objectives; anomalies are analyzed to determine whether they represent security events.”
(AICPA’s 2017 Trust Services Criteria)
While you have logs, a key challenge is that they are spread across your cloud storage, data lakes, EDR, identity providers, and more.
Federated Detections and Federated Search will allow you to correlate and investigate data across your data mesh to trigger alerts and demonstrate real-time monitoring—without centralization.
HIPAA Security Rule – 164.312(b):
”Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.”
Organizations that need to comply with HIPAA have to show who accessed patient records, when, and from where.
A federated search solution would let you trace an identity’s activity across information systems via authentication logs and cloud infrastructure — all from one single search pane.
GDPR – Article 30:
“Each controller and, where applicable, the controller’s representative, shall maintain a record of processing activities under its responsibility. That record shall contain all of the following information …
…” (https://gdpr-info.eu/art-30-gdpr/)
To comply with the above for example, you need to answer, “Did this user access this sensitive data?”
With a Federated Search solution, you can issue a single query across your data lake, cloud accounts, and application logs for a particular user’s activity.
PCI DSS 4.0 – Requirement 10.7:
“Retain audit trail history for at least one year; at least three months of history must be immediately available for analysis.”
As we discussed earlier, logs live across cloud accounts, data lakes, endpoint tools, and more.
Using a federated search solution, you can meet audit requirements by searching across them all in real-time—without centralizing data.
SOX – Section 404:
Section 404, with its sub-sections, requires management to conduct an evaluation of the operational effectiveness of the company’s internal controls over financial reporting. (https://www.sec.gov/news/studies/2009/sox-404_study.pdf)
Proving control effectiveness often means showing consistent enforcement across applications, infrastructure, and users.
Federated Search can surface activity, access attempts, and control failures across disparate platforms, empowering faster root cause analysis.
Why SIEMs fall short with compliance-driven investigations
SIEMs were never built for centralizing the level of data that organizations generate today. To even begin searching, you need to:
- Centralize data from every source (costly ETL + storage).
- Store data in your SIEM vendor-specific format, often losing the full raw data information.
- Perform a swivel-chair analysis across 10 or so disparate browser tabs, for each data source that is not present in the SIEM.
That’s fragile and inefficient for your most expensive resource – your human capital, your security team. IAnd it is also impossibly expensive in terms of actual dollars.
Query is the Federated Search solution for your compliance needs
As the pioneer of Federated Search, Query flips the script. With its security data mesh architecture, you can search across all your existing data stores—Amazon S3, Splunk, CrowdStrike, Microsoft Sentinel, Snowflake, and 40+ common sources—without moving data. Query can work with any raw data format, so even data in its raw form is searchable. That means you can respond to compliance requests in minutes, not weeks.
With Query, what does a compliance inquiry look like in action
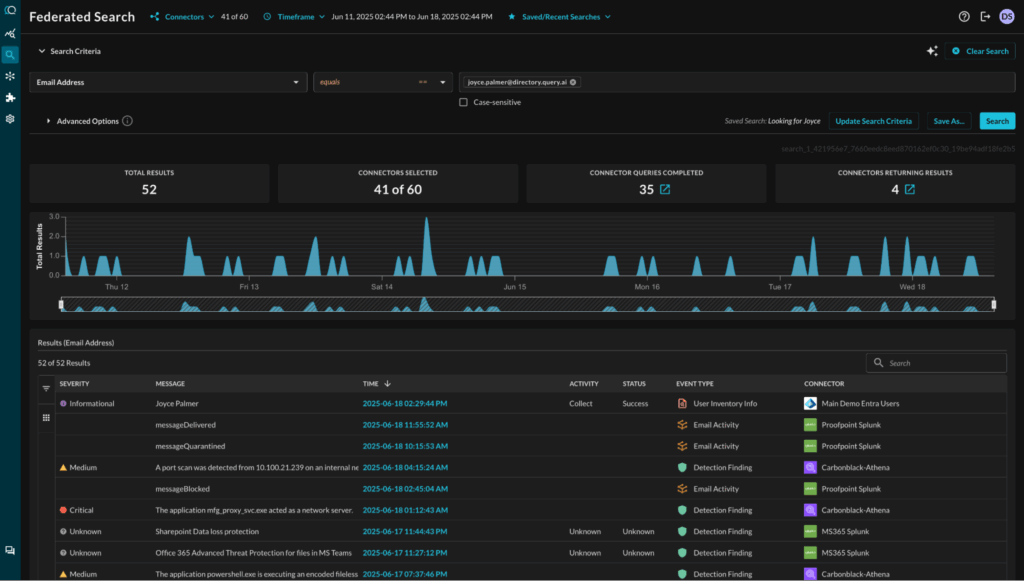
Let’s take a scenario: A GDPR data subject access request (DSAR) lands in your inbox. You need to identify all systems where “jdoe@example.com” accessed personal data.
With Query:
- Run a federated query across your sources for Email=jdoe@example.com, for example, Snowflake data lake, Okta identity logs, and AWS CloudTrail—all at once.
- Query normalizes search results in real time and combines data from across remote sources.
- Query delivers a complete result in minutes. You meet regulatory timelines, avoid fines, and demonstrate compliance maturity.
Why compliance teams love Query
✅ Unified Audit Trail Timeseries – Build full-fidelity timelines from disparate systems, no matter where the data lives.
✅ Retain Data Where It Is – Reduce cost and complexity by avoiding redundant pipelines or SIEM ingestion.
✅ Schema-Agnostic Search – No need to normalize before searching; use federated search across structured and semi-structured data.
✅ Blazing-Fast Investigations – Respond to audits, DSARs, and internal control assessments in minutes, not days.
✅ Scalable by Design – Handle multi-cloud, multi-region, multi-tool environments without vendor lock-in.
Ready for Federated Search?
Compliance doesn’t have to be a fire drill. It also does not need to be as expensive to plan and operationalize. With Query Federated Search, you can flip the script from reactive scrambling to proactive readiness.
Bonus: It’s not just for compliance. The same federated architecture accelerates threat detection, hunting and investigations, and incident response. One interface. All your data. Free from headaches.
Want to See It Live?
Let us show you how Query can simplify your compliance workflows and reduce audit fatigue and costs. Request a demo →.

