Read on for an intriguing glimpse into the history and evolution of what has in recent years become a top concern for CISO’s globally.
Photo by Markus Spiske on Unsplash
What is Ransomware?
The threat of another large scale attack is always present for businesses, people, and yes, even governments. Hopefully I can share a little information on what ransomware is, where it came from, how it works, and maybe shed a bit of light on the topic before the next attack.
Ransomware is a lot of things: scary, frustrating, debilitating, illegal, and most surprisingly, capable of making over a billion dollars in payouts annually. What’s even worse is how much it costs businesses and people to deal with ransomware, possibly as high as $75 billion each year. This estimate may seem high compared to the $1 billion in payouts, but just think about what is even more valuable than money. The answer of course is time. These businesses are forced to spend unbelievable amounts of time on finding a solution, rebuilding software and records, and playing catch up for months or even years.
Malware has been around for nearly as long as computers, with some of the earliest versions dating back to the 70s. Of course, the spread was much slower and very easily contained. But, here we are today, only a handful of applications lack a graphical user interface. Gone are the days of the command line interface, and gone are the days of slow, easily contained malware.
First Record of Ransomware
It was only a matter of time before people realized that computers and malware could be combined to make some serious money. In 1989, this is exactly what Dr. Joseph Popp did, although he claimed that all money extorted would go to AIDS research. Popp handed out and mailed upwards of 20,000 floppy disks with a survey that would tell the users their risk of contracting the AIDS virus based on their answers. What the recipients didn’t know was that the software came with a price.
This first occurence of ransomware contained many of the basic principles that we see in today’s versions. The software mocked and threatened the user, demanding money in return for their data, which had been encrypted. However, Popp’s methods would have little to no traction in the world today. He asked the ransom to be sent to a PO Box in Panama, which would almost certainly trace back to him, and even further, the encryption method only attacked the file names, so users’ file data was still intact.

AIDS Trojan Ransomware
Advancements in Ransomware
Just as quickly as experts were learning about existing malware, developers were creating new strains and families. For ransomware, this culminated in 2006 with the Archievous Trojan, which encrypted all of the files in the ‘My Documents’ folder (not just the file names this time). This was also the first ransomware virus to use asymmetric encryption, which meant that there was a key to encrypt the data and a separate key was needed to decrypt, a departure from Popp’s symmetric encryption.
Following a short lull the next major step in ransomware development came in 2011, along with the creation of anonymous payment websites. This meant cyber criminals could get payments quicker and much safer — no need to use PO Boxes in Panama anymore. We also saw the WinLock Trojan, another departure from traditional ransomware up to this point. WinLock is of the ‘Locker’ types of ransomware, meaning it locks the computer so users can’t even log in unless they pay the ransom. In the case of WinLock, only the locker (restricted access) strategy was applied, files were not encrypted in any way.
Once the locker strategy was found, there was one piece missing to really push users into paying the ransom, and that lied in understanding the psychology of a user.
Playing on that phycological understanding we saw the advent of new scareware and ‘Police’ Ransomware. This version of ransomware would lock down the user’s computer claiming the user had participated in illicit or illegal activities. The software also posed to be coming from an official law enforcement agency or even the FBI in the case of Reveton. Some strains of police ransomware would even take over the webcam to display a live feed of the user, insinuating that they are being watched.
Undoubtedly, the goal of this software is to scare the user enough that they don’t even think to ask somebody for help they just act and pay the ransom.
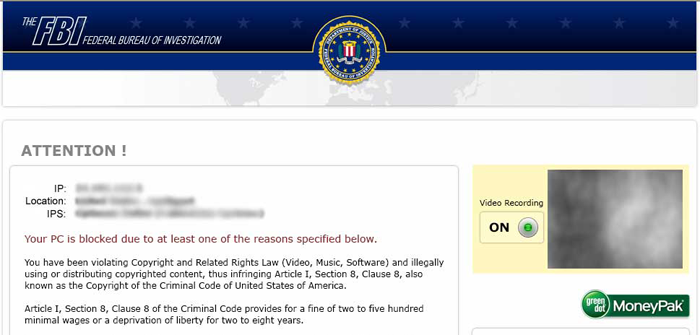
A sample of a Reveton ransom message
Then again there was a small stretch of time where seemingly little advancement was being made to the development of new ransomware, that is, until the widely publicized release of CryptoLocker came into play.
In late 2013, we saw new methods of delivery and a much more direct and threatening means to incentivize payment. CryptoLocker was now spreading through a network of infected or ‘zombie’ computers, infecting websites and exposing more users than ever. The inventors of CryptoLocker even employed advanced spear phishing techniques, where they would email businesses with legitimate-looking complaints or offers, within the attachments of those messages was hidden CryptoLocker software. Upon opening unsuspecting users would then find their files had all been encrypted with a message plainly stating that their files were encrypted and they had three days to pay the ransom or everything would be deleted.
Ransomware stayed in a similar vein to CryptoLocker for the next few years, with some small variations; being able to encrypt multiple operating systems, including android, new payment methods(mainly bitcoin), and cryptoworms, which are ransomware that are able to spread automatically through networked devices.
All of this sums up to the current state of ransomware today.
Ransomware as we Know it
Today we see the culmination of all this badness. A clear evolutionary result of all past ransomware with the best (worst) parts of each stiched together. This combination has enabled recent variants you’ve certainly heard of like WannaCry.
Short for WannaCrypt. WannaCry takes advantage of a leaked zero day security flaw in older versions of Windows Server. This gave it the power to spread globally and fast.
Perhaps more shocking is that this particular flaw exploited by WannaCry was discovered and kept hidden from Microsoft for over 5 years.
We are now seeing a newer models for profiting from ransomware ironically following other software business trends known as ransomware-as-a-service.
Developers are offering their ransomware to anybody who is willing to pay for it; just change the address for payment and communication and the buyer is ready to extort some Bitcoin from unsuspecting users and businesses.
The 2019 attack in Baltimore was carried out with a ransomware variant known as Robbinhood, and some experts believe that this large scale attack is meant to draw attention to the name so it can be offered in the future with the ransomware-as-a-service model.
What can we do?
The answer is quite simple. Disconnect from the internet, forever. But really, if that is a little too big of a jump for you, I understand. I’m sure not going to do that.
What we can do is practice good cyber hygiene. We can stay on top of security updates, be careful of what we download and what websites we visit, always keep offline backups, even something as simple as knowing what ransomware is puts you ahead of those who don’t.
There is also the question of whether or not to pay the ransom, if you are unlucky enough to be hit, for the greater good its easy to say, you shouldn’t! Paying just incentivizes this behavior, and in some cases even after payment the user is still left with a crippled system (who would have guessed it…a dishonest criminal).
That being said, situations vary and in the event you are faced with this unfortunate choice, you’ll have to weigh your options. If you’re unprepared or caught of guard it would be very hard to start over from square one with everything. All your files, photos, contacts, assignments, anything saved to your computer and the thought that its suddenly just gone.
That’s tough to put a price on, but luckily(or not) the ransomware developers tend to do that part for us.
So now you have enough information to be Terrified On The Internet™. Use this information to your benefit, do your research, follow good security practices, and encourage others to do the same.
Either way, be safe out there!


