USE CASE
Have Your Splunk and Eat It Too
Extend Splunk’s reach and cut its costs. Query lets you keep the workflows you rely on, while extending visibility to security data wherever it lives: another SIEM, cloud storage, a data lake or at the source.
Splunk Works. The Economics Don’t.
Splunk is the workhorse of many SOC teams. Analysts depend on its search, visualization, and detection capabilities. Customers love Splunk but they hate their Splunk bill.
Cost pressures usually drive organizations toward two options:
“What are the Splunk alternatives?”
“We have to cut our Splunk costs!”
The challenge isn’t that Splunk doesn’t work well. It’s that the economics don’t. Data volumes keep growing. Splunk ingest and compute costs climb even higher. Teams are forced into painful trade‑offs: reduce what’s ingested and limit visibility, or explore a risky move off the platform entirely.
Cut Splunk Costs. Expand Your Visibility.
Most SIEM migrations follow a centralization mindset: move everything from one high-cost platform into another. Query enables a different approach through federation. Instead of forcing all data into a single location, federation lets you store and query each dataset from the most fit-for-purpose location.
- Slash Splunk Costs, Expand Your Visibility
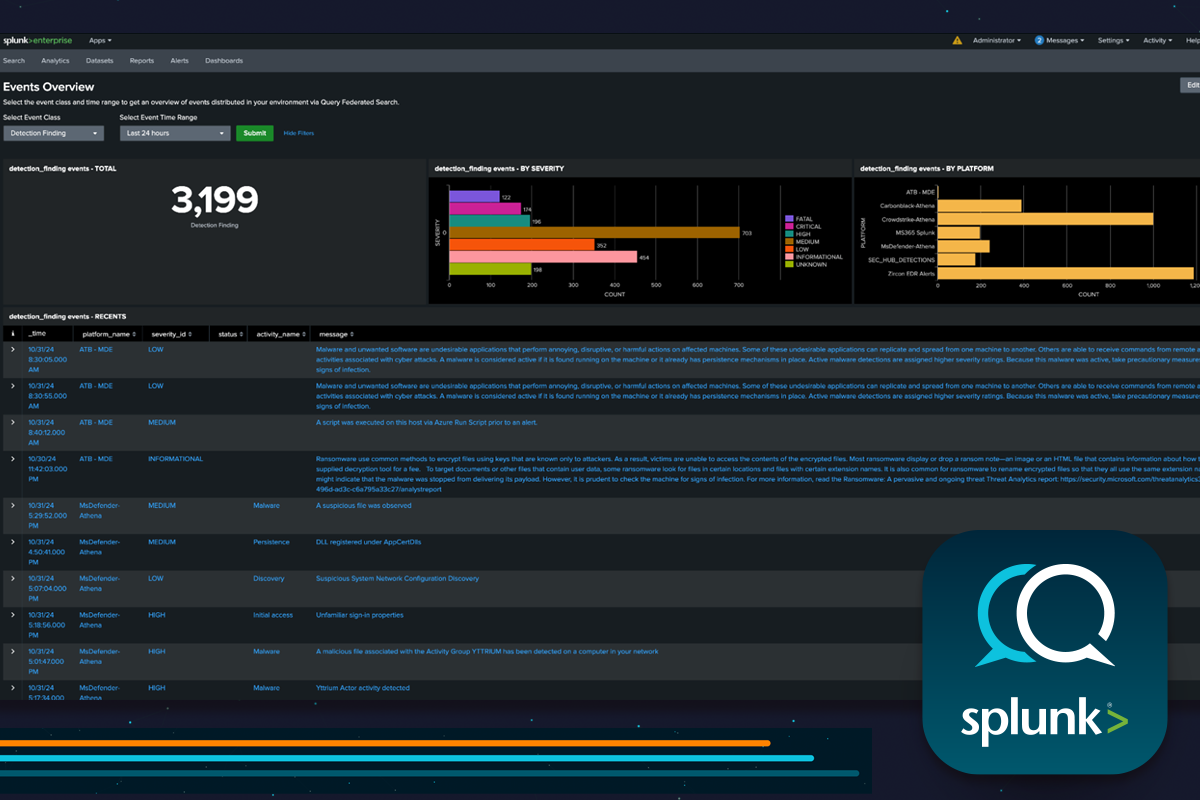
Query federates Splunk access to any connected data source. You can reduce ingestion and storage costs while querying security-relevant data wherever it lives. - Faster Investigations, Threat Hunting, & Incident Response
The Query Splunk App eliminates manual correlation and pivots outside of Splunk. All the context and enrichment data analysts need, delivered in the familiar Splunk console. - Extend your Splunk Dashboards & Detections
Query extends access to distributed data, making dashboards more powerful, triggering alerts from any Query‑connected source, and enabling higher-fidelity detections. - Land Data Where You Need It
Write clean, compressed security data directly to the storage destination of your choice, ready for investigations, analytics, or compliance use cases with Query Security Data Pipelines.
Query turns it all into a security data mesh so analysts can search and work across all sources.
Connect Splunk to the
Query Security Data Mesh
Install the App
Download Query Federated Search from Splunkbase and install it in your Splunk tenant.
Connect Your Data Sources
Connect over 50 supported data sources to create your security data mesh.
Start Querying
Search, visualize, and detect across Splunk + everything else. All from the Splunk console, without the need to ingest data.